
Julian Meloni
Feb 6, 2020
Handling the risk that ransomware poses is a difficult challenge for companies and IT security teams in all industries. The biggest threat ransomware possesses is the encryption of file shares that users have access to, as well as, the associated potential for data loss and business down time. Usually people often identify ransomware when it is in the process of encrypting these shares. The problem is that you need to identify the source quickly in order to prevent further damage or ensure that the process does not repeat when backups are restored.
But what is the best way to find the source system of infection? REAL’s security team are often asked this very question and so we have prepared the following information to help people identify and stop these incidents as quickly as possible.
Check The Ownership Of The Files
When Ransomware encrypts a file, it usually takes ownership of it, and typically will create a ransom note. The most effective way to find the source of the attack is to identify the file owner’s domain user account from which the ransomware is being created. Then find the computers on the network that are logged into that account.
You now have two options to do immediately:
- Physically isolate the infected computer from the network.
- Revoke the user account’s access to shares.
Now to identify the owner, open the file properties of the file:
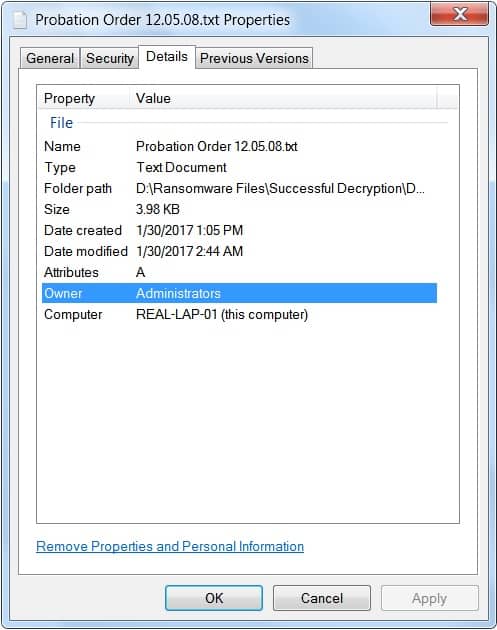
Alternatively, you can also do this via PowerShell. This can be used to identify the owner as well using GET-ACL against one of the encrypted files or ransom notes:
GET-ACL C:\filename of ransomware.txt | Select Owner
You may encounter that the security identifier (SID) is not resolving to a username. There are a number of methods to resolve a user SID:
WMI (in command line):
wmic useraccount where sid='S-4-3-13-533586589-123956121-5342564793-1631’ get name
PowerShell – Domain Environment:
$strSID="S-4-3-13-533586589-123956121-5342564793-1631"
$uSid = [ADSI]"LDAP://<sid=$strsid>"
echo $uSid</sid=$strsid>
Now you figured out the username, you need to find the actual computer that the user account is currently logged in from. Remember the “Remote Server Administration Tools for Windows” must be installed with the “Active Directory Module for Windows PowerShell” and have that enabled.
NOTE: Searching this way may take a large amount of time depending on the size of your network domain.
$Computers = Get-ADComputer -Filter {Enabled -eq 'true'} ForEach ($comp in $Computers) {$Computer = $comp.Name Write-Host "Querying $Computer" $csvTmp = quser /server:$Computer | ForEach { (($_.trim() -replace "\s+",","))}
$queryResults = (($csvTmp -split '\n')[0] + '-2' | Out-String).trim() + "`n" + ($csvTmp | Select -Skip 1 | Out-String).trim() | ConvertFrom-Csv ForEach ($queryResult in $queryResults) {$User = $queryResult.USERNAME If (($User -match "[a-z]") -and ($User -ne $NULL)) {Write-Host $Computer logged in by $User on session type $sessionType $SessionList = $SessionList + "`n`n" + $Computer + " logged in by " + $User}}}
$SessionList | findstr "USERNAME"
Now, network and system administrators should be able to assist in identifying the physical host based on the network architecture, subnet, and through querying network infrastructure devices.
In addition, if the attack is currently ongoing, there are other options to find active sessions and open files in Windows Server environments.
Active user sessions:
Computer Management -> System Tools -> Shared Folders -> Sessions
Open files: (Users with shared files that are currently opened)
Computer Management -> System Tools -> Shared Folders -> Open Files
How To Prevent Ransomware
With ransomware becoming more common every day, the requirements for protection, as well as, a comprehensive response plan for these types of incidents is of the number one priority. Determining the origin of the ransomware, isolating the source, and revoking the affected user’s access to shares may stop the encryption that is already underway, however, this requires a rapid response. During every second that source system is being tracked down, business critical data are being encrypted for ransom. If this happens off-site hours, than most likely will walk into this mess in the morning.
This article does not take in to account cases where a more targeted and manual approach is used by an attacker, which is a trend that REAL is seeing becoming more common. Attackers perform reconnaissance within the business, move laterally across the network when an exploit is found and utilized, destroy online backups, focus encryption of high-value targets within the domain, using multiple points of origin simultaneously to speed up the encryption process, and thereby reducing the amount of time available to respond and contain the incident. In cases like these though, more in-depth investigation are required to determine the origin of the attack and contain live attackers on the network.
As ransomware attacks become more advanced, more appropriate security controls need to be in place to aid in protecting organizations from these threats. While identifying the source of an attack is critical to ensuring that no further damage is done, having set-up a defense and response solution to stop ransomware in its tracks is the first step.
With all this in mind, REAL has developed a detailed strategy with multiple polocies and procedures, which uses a combination of machine learning, behavioral analysis, and many other methods to identify ransomware and stop it before infection. When an attack is identified, we immediately interven to protect the data and the endpoint by stopping the ransomware in its tracks outside the network.
By allowing us to put our polocies and procedures in place, IN ALL AREAS, you will not have to worry at all. Remember, we pride ourselves on, that thus far, none of our clients have been breached by ransomware, hackers, or viruses.
Please reach out to us to see how REAL Solutions Technologies can help secure your network so Ransomware is no longer a worry to your business.
